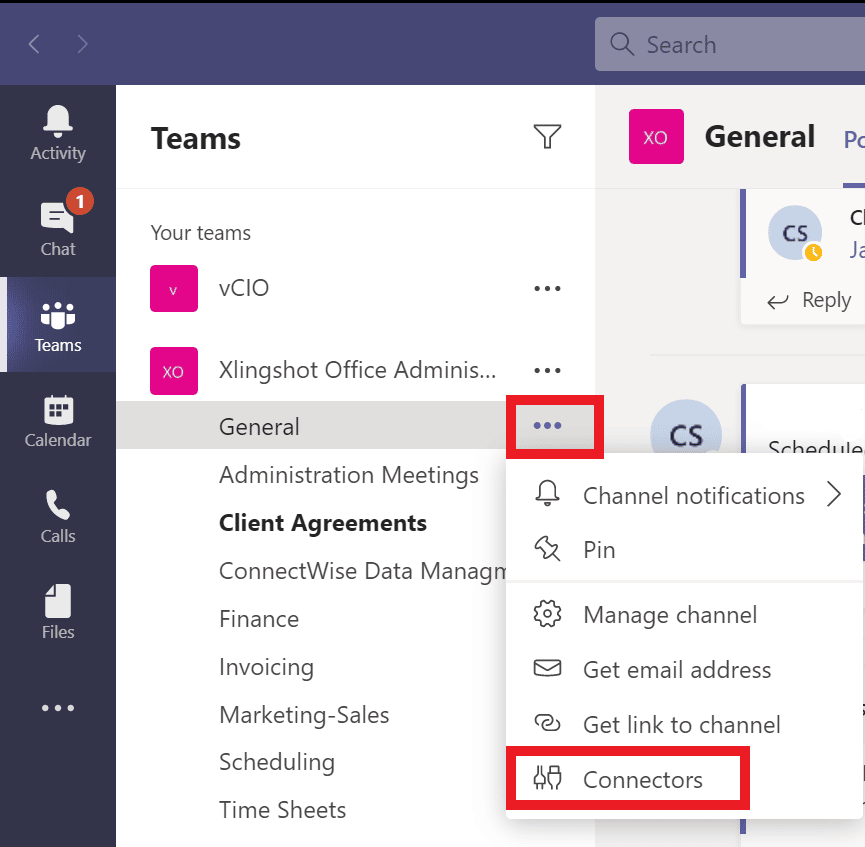
How to Add a Connector to an MS Teams Channel
admin_hosting2022-02-20T14:15:34-07:00Connectors in MS Teams are a very useful function but few users know about them. You can use connectors to sync updates and data into the chat stream in Teams from other services that your organization subscribes to, such as Trello, Wundlist, GitHub, and Azure DevOps. You can also set up connectors to sync data from your other Office 365 programs into the chat stream. For example, we have a client who wanted to set up automated updates between the sales team and the accounting team when new clients are signed. They created a connector to forward all email notifications that a new contract has been signed into the accounting channel in Teams. They could have set up the email [...]