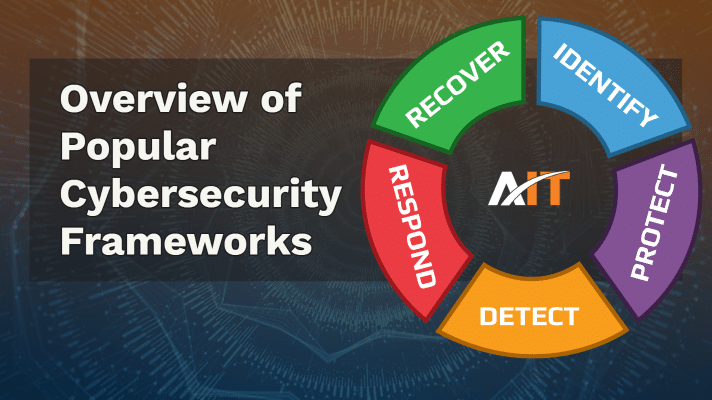
Vendor Management in Cybersecurity: Selecting the Right Partners
marketing@accountabilit.com2024-11-22T12:28:24-07:00The Real-World Impact of Vendor Management in Cybersecurity Did you know that in 2020, the SolarWinds cyber-attack, which affected numerous government agencies and companies, was attributed to a compromised update from a trusted vendor? This real-life incident underscores the significance of vendor management in cybersecurity. In today's digital landscape, businesses face multifaceted cyber threats that can lead to massive financial loss, reputational damage, and daunting legal liabilities. One of the principal strategies for building a robust cybersecurity defense is selecting the right vendors equipped to fortify your IT infrastructure. Why is Vendor Management Critical in Cybersecurity? The 2013 Target breach, where attackers accessed the company's network through an HVAC contractor, further exemplifies the paramount importance of vendor management. Such [...]